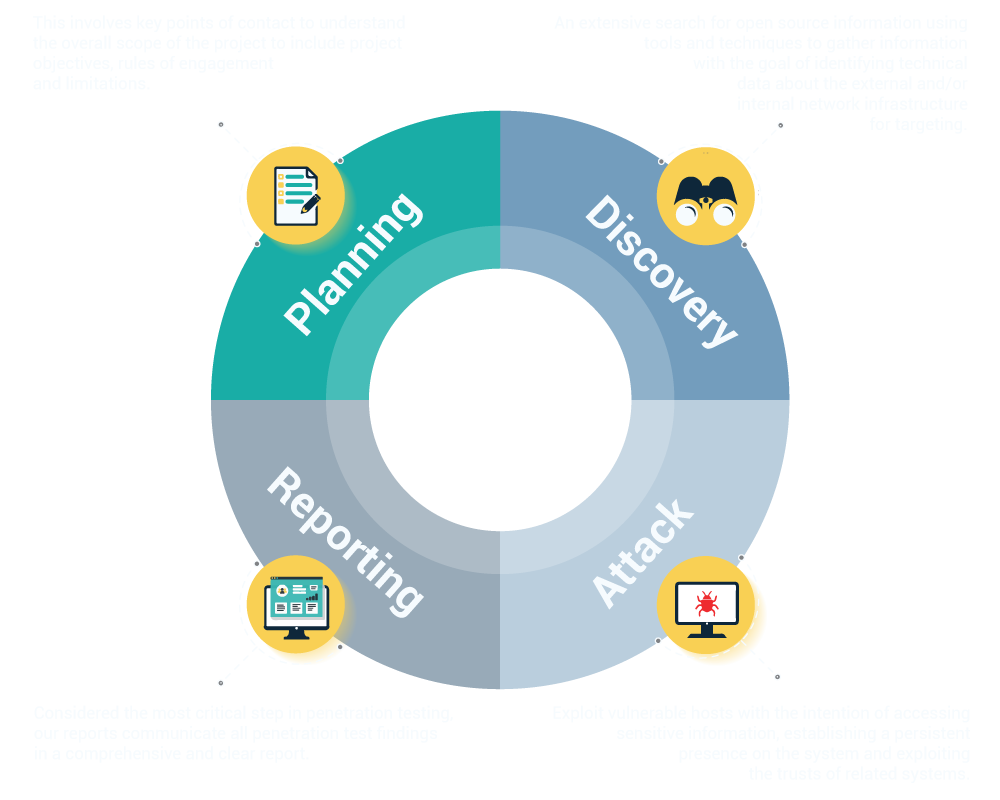
are there holes in your network?
Penetration Testing
are there holes in your network?
Penetration Testing
Security You Can Count On
Network Penetration Testing
Port
Mapping
Unauthorized Access to Sensitive Data
System
Identification
Firewall
Probing
Known Vulnerability Analysis
Active Defense Evasion
Service
Mapping
Internet
Mapping
Identify Vulnerabilities and Exposures
Penetration Testing evaluates your organization’s ability to protect it’s network, servers, applications, secure encrypted connections, external routers, email systems, firewalls, and end-users.
By performing penetration tests you can gain insight on the overall health of your network, applications and security layers. This allows your organization to prioritize on remediation, apply needed security measures and allocate security resources more effectively.
Pen tests allow organizations to leverage a proactive security approach, uncovering weaknesses so that organizations know what remediation is needed, and if additional security measures should be implemented.
Gain visibility into your environment and determine how successfully network defenses perform when faced with an attack. Intelligently allocate security resources to improve protection.
Increase confidence in your security strategy by quantifying the need for more significant investment in security technology.
Our Process